Tuesday, June 26, 2007
Forget those hard to remember passwords?
It will remember your website passwords, forum passwords or any websites that require you to login. its will automatically detect when you are logging in with the username and password, once you do so and you have successfully logged in (Most of the time), it will remember it from there on.
You can download it here for a limited time: http://www.roboform.com/pcw (Thank you PcWorld)
or you can visit their website at: http://www.roboform.com/ and download the free one (Unlimited Time). (I don't know if there is a difference between the 2 download areas, i suggest you use the PcWorld Download While it lasts, or you can get it at their homepage.)
I use this to login to my blog, my forums, to my websites and anything else that requires a login. (So far i have not noticed any way for it to remember you logging into any program on your pc, only websites)
It is Vista, and Internet Explorer 7 supported.
It will also work in Firefox.
Analysts: Vista SP1 Delay Won't Hurt Businesses
Any delay shouldn't affect adoption of Windows Vista by enterprises, analysts say.
Elizabeth Montalbano, IDG News Service
Although Microsoft Corp. may not have the first service pack for Windows Vista ready at the end of this year as some expected, financial analysts say that a delay should not have a negative effect on enterprise adoption of the OS.
Many large enterprise customers have said they will wait for the first service pack for Vista to deploy the software across their companies. Some were expecting SP1 before the end of the year after Microsoft Senior Vice President Bob Muglia said in a published report last November it would be released with Windows Server code-named Longhorn, due by the end of 2007.
However, rumors swirled last week that the release of the pack would be pushed into 2008 after Microsoft said in a court filing dated June 19 it would have only a test version of Vista SP1 out before the end of the year. According to the document, filed as part of the ongoing antitrust case with the U.S. Department of Justice, the software is to be released by then to answer a complaint by Google Inc. that claims the OS' built-in desktop search capability interferes with the use of Google's competing search technology.
The rumors caused investors to worry about enterprise adoption of Vista being pushed further out, and company stock declined 2.4 percent Friday, opening at US$30.03 and closing at $29.54.
UBS Investment Research analyst Heather Bellini tried to allay investor fears in a research note published Monday, saying that the end of the year release of a beta listed in the document "probably represents a 'drop-dead' date."
"The company most likely has accounted for the possibility of unforeseen delays in this timing," according to Bellini's note. "As such, we believe Vista SP1 could be available sometime before the end of the year barring any material delays."
Andrew Brust, chief, new technology, for consulting firm and Microsoft partner Twentysix New York, who is familiar with the company's plans, said he also believes Microsoft will have SP1 out the door before the end of 2007. He would not disclose specifics, but Brust said that what he's heard "contradicts the chatter."
"Microsoft is quite aware of the need to get an SP out there; I promise you that," he said in an e-mail interview Monday.
Through its public relations team, Microsoft said Monday that it has never committed to a release date for SP1, and confirmed the company will be releasing test builds of the software from now throughout the end of the year. Despite Muglia's comments last year, even a 2008 release for Vista SP1 should not be considered a delay because the company never announced a firm date for release, Microsoft said.
Enterprises are most likely waiting for the release of Windows Server Longhorn -- now known by its official name, Windows Server 2008 -- before deploying Vista, making SP1 less relevant to enterprise deployment than some think, according to a research note from Citigroup Global Markets.
Security Vendors Challenge Antivirus Tests
Makers of security software question the thoroughness and accuracy of evaluations.
Jeremy Kirk, IDG News Service
Antivirus software is frequently tested for performance, so picking a top product should be straightforward: Select the number-one vendor whose software kills off all of the evil things circulating on the Internet. You're good to go then, right? Not necessarily.
The increasing complexity of security software is causing vendors to gripe that current evaluations do not adequately test other technologies in the products designed to protect machines.
Relations between vendors and testing organizations are generally cordial but occasionally tense when a product fails a test. Representatives in both camps agree that the testing regimes need to be overhauled to give consumers a more accurate view of how different products compare.
"I don't think anyone believes the tests as they are run now ... are an accurate reflection of how one product relates to the other," said Mark Kennedy, an antivirus engineer with Symantec Corp.
Representatives of Symantec, F-Secure Corp. and Panda Software SA agreed last month at the International Antivirus Testing Workshop in Reykjavik, Iceland, to design a new testing plan that would better reflect the capabilities of competing products. They hope all security vendors will agree on a new test that can be applied industrywide, Kennedy said.
A preliminary plan should be drawn up by September, Kennedy said.
One of the most common tests involves running a set of malicious software samples through a product's antivirus engine. The antivirus engine contains indicators, called signatures, that enable it to identify harmful software.
But antivirus products have changed over the last couple years, and "now many products have other ways of detecting and blocking malware," said Toralv Dirron, security lead system engineer for McAfee Inc.
Signature-based detection is important, but an explosion in the number of unique malicious software programs created by hackers is threatening its effectiveness. As a result, vendors have added overlapping defenses to catch malware.
Vendors are employing behavioral detection technology, which may identify a malicious program if it undertakes a suspicious action on a machine. A user may unwittingly download a malicious software program that is not detected through signatures. But if the program starts sending spam, the activity can be identified and halted.
Also, a program can be halted if it tries to exploit a buffer overflow vulnerability, where an error in memory can allow a bad program to run. Host-based, intrusion-prevention systems, which can employ firewalls and packet inspection techniques, can also stop attacks.
The ways in which a computer can be infected also make comprehensive testing complex. For example, users may infect their computers by opening malicious e-mail attachments or visiting harmful Web sites designed to exploit known vulnerabilities in a Web browser.
The different modes of attack also involve different defenses, all of which would need to be tested to arrive at an accurate ranking, analysts said.
By contrast, signature-based tests can take as little as five minutes. "This is a very basic test," said Andreas Marx of AV-Test.org, who wrote his master's degree thesis on antivirus testing. "It's easy, and it's cheap."
Other concerns remain, over sample sets of malicious software, the age of the samples and the relative threat those samples pose on the Internet as they become older. Security vendors also think tests should check how well security applications remove bad programs, a process that can affect a computer's performance.
For vendors, a failed test can be embarrassing, since the testing companies often issue news releases highlighting the latest results.
Testing companies make money in various ways. AV-Test.org is often commissioned by technology magazines such as PC World (a magazine owned by IDG). Virus Bulletin licenses its logo to companies for use in promotional material and publishes a monthly online magazine.
Earlier this month, Virus Bulletin announced that its latest round of testing produced some "big-name failures," including products from Kaspersky Lab and Grisoft SRO.
The company's VB100 tests antivirus engines against malware samples collected by the Wildlist Organization International, a group of security researchers who collect and study malware. To pass the VB100, products must detect all samples.
Kaspersky briefly removed a signature for a worm out of its product for "optimization" purposes on the day of the test, wrote Roel Schouwenberg, senior research engineer for Kaspersky, in an e-mail. The signature has since been put back in, he said.
"Obviously, we would have rather passed than failed," Schouwenberg wrote. "Had the test been conducted a day earlier or a day later, we would have passed."
Similarly, F-Secure initially failed its test also because of a technicality, but the failed rating was later reversed. All vendors are told after testing which samples they failed to detect, thus most end up adding signatures to their products.
So what should a user do? John Hawes, a technical consultant for Virus Bulletin, cautioned that the signature-based tests are "not enormously representative of the way things are in the real world."
But Hawes also noted that signature-based tests can indicate the reliability and consistency of a vendor's software. Virus Bulletin also writes reviews of AV suites, which take into account aspects such as usability, which may be just as important as detection for consumers. The company is developing more advanced tests that will test new security technologies.
AV-Test.org is already performing more comprehensive tests, although it uses between 30 to 50 malware samples, a much smaller sample set compared to the Wildlist, which uses more than 600,000 samples, Marx said. Those tests may give a better indication of how a security software suite performs.
At a bare minimum, through, users should install some security software, as computers without it can face high risks, Marx said. Several free suites are available that may be fine for light Internet use, he said.
Ironically, Marx doesn't use any antivirus software. That's because AV-Test.org collects malware for its testing, most of which comes through e-mail from other researchers. "I'm getting about 1,000 viruses a day," he said. "It [antivirus software] would be counterproductive."
Monday, June 25, 2007
Firewall Program results
http://www.firewallleaktester.com/tests.php
(Scroll to the bottom and hit view results)
Zone alarm is the third best in firewall leak testing (Scroll down the page and look at the bars). Now as you probably noticed, these tests weren't done on vista. Although there isn't much of a difference between Vista and XP when we are talking about firewalls. So if I were you, and you are running Vista, I suggest that you keep Windows Vista's firewall on, along with what ever else you choose to use.
Vista Built in Firewall Results
-------------------------------------------------------------------------------------------------
Impact on the leaktests
As you have read, the default 'out of the box' Vista security is very different than Windows XP, and brings some improvements. Below we will see per leaktests the impact on them, if any. The test will simply consist of running the leaktest, without any third party security software installed (no personal firewall, no HIPS), under an administrator account. All tests are done under Windows Vista Ultimate 64bits, with DEP enabled. DEP is not new to Vista, it already exists into Windows XP Service Pack 2 (SP2), Windows XP Tablet PC Edition 2005, and Windows Server 2003.
The tests requiring Internet Explorer are done with IE 32bits, as it is the version that all Vista editions have by default, even on Vista x64. The built-in firewall is left to default settings, blocking only inbound.
Result : 9 leaktests are blocked on Vista, 3 weren't tested due to not being compatible or because WinpCap not being installed (WinPcap 4.0 or newer is required on Vista x64), and 12 leaktests are still working despite new Vista's security features. That means that 37,5% of the leaktests are blocked either from running properly, or from making a successfull outbound leak.
If you look differently the same numbers, we can say also that 50% of the leaktests (12) only are sucessfull on Vista, so that half are blocked (12 on 24). Pick the statistic you prefer.
-------------------------------------------------------------------------------------------------
So i (HotShot) suggest you get a second firewall, I personally use Zone Alarm Free with my Windows Vista Home Premium. Works like a charm and amazingly doesn't seem to lag me. Although make sure you go into the settings and allow all the programs you commonly use like Firefox or IE etc... Zone Alarm Comes out to be the 3rd best in Leak Testing. I will post that later on, but for now, this is what vista users need to know when they are looking for firewalls.
Sunday, June 24, 2007
Vista DRM Precludes Virtualization?
DRM restrictions may have caused Microsoft's Vista virtualization flip-flop.
Eric Lai, Computerworld
Sunday, June 24, 2007 9:00 AM PDT
Conspiracy theorists may link Microsoft Corp.'s abrupt decision late Tuesday not to remove restrictions on consumers virtualizing its Vista operating system to a Department of Justice agreement announced the same day or to a desire to jerk Intel Mac users around.
But the actual reason may be found in three little letters: DRM.
Vista's new digital rights management features enable movies or music files to be password-protected or made accessible only to authorized users for opening, viewing or changing.
Whether most users would call DRM a feature, however, is questionable. A close cousin to DRM technology, known as Windows Rights Management Services (which in turn is part of a larger category of technologies called Enterprise Digital Rights Management, or ERM), can help business users password-protect key documents and files, or assign the ability to open them only to trusted co-workers. But DRM's main purpose seems to be to help the Warner Bros. and Sony Musics of the world keep consumers from sharing movies and music. The entertainment industry claims that almost all blocked sharing is illegal; digital rights watchdogs argue that legitimate consumer uses are also blocked by such technology.
DRM is capable of blocking both overt piracy -- distributing movies via BitTorrent and other peer-to-peer networks -- as well as other common scenarios that most consumers do not consider piracy, such as moving legally acquired music files from their desktop PCs to their notebook computers.
"It's like when you batten down the hatches on a ship in a storm," said Aram Sinnreich, an analyst at Radar Research in Los Angeles. "Vista wants to batten down every software or multimedia bit so that they don't go somewhere the creator doesn't want it to go."
Versions out of control?
The problem is that virtualization, by accident, appears to break most of Vista's DRM and antipiracy schemes.
Virtualization software -- think VMware Inc.'s VMplayer, Microsoft's Virtual PC or Parallels Inc.'s Parallels Desktop -- allow computer users to boot one operating system but run a second one as a "guest" at the same time.
That can allow a user who has booted Windows Vista to load XP-only applications in a guest XP operating system, also known as a virtual machine (VM). Or it can let a user with an Intel Mac boot up the OS X operating system but also run Windows Vista or XP applications at the same time.
Microsoft's original plan was to announce on Tuesday changes to the contracts, known as End User Licensing Agreements (EULA), for its Vista Home Basic and Home Premium editions. Those changes would permit buyers who use those editions to create VMs. The change was purely to the EULA; there is no technical limitation preventing knowledgeable users from virtualizing retail versions of Home Basic or Home Premium.
Microsoft only allows full retail versions of Vista Business or Vista Ultimate (as well as Vista Enterprise for big corporations) to run as virtual guests of a host PC. Vista Business and Ultimate cost $299 and $399, respectively. The simple change in Microsoft's license for the two cheaper editions -- Home Basic Edition and Home Premium Edition cost $199 and $239, respectively -- would have saved customers at least $60 and up to $200.
In addition, Microsoft planned to permit the use of DRM, IRM (Information Rights Management) and Vista's storage encryption technology, BitLocker, in a VM for any version of Vista.
Besides boosting flagging perceptions of Microsoft's overall virtualization strategy, the move would have made Vista virtualization much more attractive to a key and growing segment -- Intel Mac owners who want to run Windows software.
But at the last moment, Microsoft did a 360. Its explanation was terse: "Microsoft has reassessed the Windows virtualization policy and decided that we will maintain the original policy announced last Fall," said a spokesman in an e-mailed statement.
A perfect picture (of cross-purposes)
When a user creates a VM, the virtualization software takes a snapshot of the PC's hardware and then creates an exact copy of how that works in memory, according to DeGroot.
This ability to perfectly simulate the way the original PC ran (albeit more slowly than the original) is why VMs are such a useful tool. But a VM, once created, can be copied hundreds or thousands of times and ported over to radically different PCs without triggering the antipiracy and DRM schemes of most software or multimedia files, including Vista's. Those schemes raise red flags only if they realize they've been moved to another computer, DeGroot said.
Analysts say what probably happened behind the scenes is that Microsoft or one of its media partners decided at the last moment that encouraging consumers to use virtualization would, at least symbolically, be at odds with its attempts to enforce DRM.
"Microsoft doesn't want the music labels, TV networks and movie studios to come back to them and say that you are enabling this ability to move content around," said Mike McGuire, an analyst at Gartner Inc.
Microsoft has more at stake than other high-tech firms, McGuire said, what with its partnerships with NBC, its Xbox gaming platform, its Media Center PCs and even its Zune music player.
"It's a very fine line that Redmond has to walk," McGuire said. "They have to answer to these companies if they want to have any hope of making the PC and their software the de facto usage model for multimedia."
The problem is that even if Microsoft -- and U.S. law -- insist it is still illegal to use virtualization to enable the sharing of software or movies or music, its antipiracy technology is powerless to stop it.
"It's absurd to expect that something demanded by a EULA is followed when technology and common practice permit otherwise," Sinnreich said. "Microsoft is banking on ongoing consumer naivete and goodwill. There will be a backlash against DRM in some not-so-distant future."
Would anyone have bothered?
Will encouraging consumer virtualization result in a major uptick in piracy? Not anytime soon, say analysts.
One of the main obstacles is the massive size of VMs. Because they include the operating system, the simulated hardware, as well as the software and/or multimedia files, VMs can easily run in the tens of gigabytes, making them hard to exchange over the Internet. But DeGroot says that problem can be partly overcome with .zip and compression tools -- some, ironically, even supplied by Microsoft itself.
"It's the kind of idea that is out there among the enthusiast community for file sharing and remixing, but it's not part of the standard arsenal for the average college student," Sinnreich said.
Gartner's McGuire agrees: "Unless virtualization is more convenient and reliable than P2P, then no one is going to go to the trouble."
Saturday, June 23, 2007
Authors Pick Of The Week
This Weeks Winning Pick is:
http://www.netvibes.com/
This is a rss/xml tracker or news page as i call it. It can keep track of your email, your local weather, your favorite news websites, this wonderful blog, PC news websites etc...
I picked it because its very simple to edit, and keeps me very organized. All you need to do is create a account, and you don't even need to activate it!
I just ask one thing, that i only suggest you do, add my blog,
http://windowscorp.blogspot.com/feeds/posts/default
Hope you like my pick of the week!
Enjoy,
- HotShot
Microsoft Sues More Hotmail Spammers
Microsoft files suit against a company and individuals accused of sending debt relief and porn spam to Hotmail accounts.
Robert McMillan, IDG News Service
Saturday, June 23, 2007 9:00 AM PDT
Microsoft Corp. has filed two lawsuits over the past weeks, looking to crack down on spam on its Windows Live Hotmail network.
The "John Doe" lawsuits were filed against unknown alleged spammers who had been sending large quantities of spam advertising debt relief and adult Web sites to Hotmail accounts.
Microsoft alleges that a company doing business under the name Consumer Solutions Network sent "misleading, deceptive, and unsolicited commercial e-mails advertising debt relief help to Windows Live Hotmail account holders."
The spam contained subject lines such as "Michelle, accounts over the limit," or "Robert, Payment not received," the suit alleges.
Consumer Solutions Network, which could not be reached for comment on this story, operates several Internet domains including myfinancialsolutions.org, consumersolution.org, and financialsolutionsonline.org, according to Microsoft.
Microsoft has also sued unnamed defendants for sending spam that promoted pornographic Web sites through Hotmail. Microsoft claims that these spammers not only flooded Hotmail accounts with unwanted messages, but also used Hotmail itself to send large volumes of spam. "Many of defendants' illegal e-mail messages were sent using... accounts obtained through false or fraudulent pretenses," Microsoft claims.
Companies like Microsoft, AOL LLC and Earthlink Inc. have launched a large number of these lawsuits in recent years, said Venkat Balasubramani, the principal of Balasubramani Law, and author of the Spam Notes blog. "They serve a deterrent purpose and they also can be a mechanism for investigation. You can issue subpoenas and dig around a little bit to find what's going on," he said.
Microsoft has filed such lawsuits on an almost-monthly basis over the past year, he added.
In April and May of this year it filed similar lawsuits against several alleged stock scammers.
These latest lawsuits were filed in King County Superior Court in Seattle. The Consumer Solutions Network lawsuit was filed on June 13. The suit relating to pornographic spam was filed on Tuesday of this week.
Friday, June 22, 2007
Microsoft Kills Longhorn Reloaded Project
Microsoft Corp. has forced developers to close down a project aimed at reviving the original Windows client code-named "Longhorn."
According to a blog posting on the site maintained by developers on the project -- called "Longhorn Reloaded" -- Microsoft sent a "cease and desist" letter to the project leaders asking them to shut it down shortly after the team posted the first release of the project online.
"It deeply saddens me that although Microsoft have known about this project for many months they only issued us with this notice a few days after we started to distribute" the first release, according to a post earlier this month on joejoe.org.Community. "I am just as sorry as you guys are about this, but we got [sic] to think about the community as a whole first."
Longhorn Reloaded Milestone 1 was released May 19 on the project's Web site, but the post informing users the project has shut down said download links and any threads about the project will no longer be active.
Through its public relations firm, Microsoft said that though the company "actively encourages and supports independent developers to take advantage of the features available in our platform to create their own applications and services," the Longhorn Reloaded project violated Windows end-user licensing.
Windows enthusiasts decided to pick up where Microsoft left off with Longhorn's development in October 2006. Microsoft had originally called the client release that became Windows Vista "Longhorn," but switched development plans and names mid project, though the company continued to use the Longhorn name for the next Windows Server release. That release has since been renamed officially to Windows Server 2008.
The Longhorn Reloaded began the project with a build called Windows 6.0.4074, which Microsoft released at its Windows Hardware Engineering Conference in 2004. Microsoft never said it actually abandoned the Longhorn client, and many predicted that when the Longhorn Reloaded project began it likely would run afoul of Microsoft's legal department.
How MySpace Is Hurting Your Network
Carolyn Duffy Marsan, Network World
Increasingly popular social-networking sites such as MySpace, YouTube and Facebook are accounting for such huge volumes of DNS queries and bandwidth consumption that carriers, universities and corporations are scrambling to keep pace.
The trend is prompting some network operators to upgrade their DNS systems, while others are blocking the sites altogether. Moreover, the "MySpace Effect" is expected to hit many more nets soon, as these network-intensive interactive features migrate from specialty sites to mainstream e-commerce operations and intranets.
"Social media is not just going to be in pure-play sites like MySpace and Facebook. It's going to become increasingly prevalent across retailers, media and entertainment," says Mike Afergan, CTO of Akamai, a content delivery network company that supports MySpace, Facebook and Friendster. "It drives a lot more requests and a lot more bit-traffic across these networks."
The demanding nature of social-networking sites was highlighted in May when the Department of Defense announced it was blocking worldwide access to 13 Web sites, including MySpace and YouTube.
"The Commander of DoD's Joint Task Force, Global Network Operations has noted a significant increase in use of DoD network resources tied up by individuals visiting certain recreational Internet sites," Army General B.B. Bell said in a memo. "This recreational traffic impacts our official DoD network and bandwidth availability, while posing a significant operational security challenge."
The Defense Department began blocking access to these sites on May 14 on its unclassified IP network, which is called NIPRNET for Non-secure Internet Protocol Routed Network.
The military isn't the only organization to notice how taxing these sites are on network resources.
"One of the things we're hearing more and more from carriers is that social-networking sites like MySpace and YouTube are contributing to an exponential increase in DNS traffic," says Tom Tovar, president and COO of Nominum, which sells high-end DNS software to carriers and enterprises.
Social-networking sites create large volumes of DNS traffic because they pull content from all over the Internet. Most of these sites use content-delivery networks to extend the geographical reach of their content so users can access it closer to home.
"A single MySpace page can have anywhere from 200 to 300 DNS lookups, while a normal news site with ads might have 10 to 15 DNS lookups," Tovar says. "It's an exponential increase."
Virgin Media, a cable service provider with 10 million subscribers (including 3.5 million broadband users) in the United Kingdom, has found that the amount of DNS traffic generated by social-networking sites has grown dramatically in the past 10 months. YouTube and Facebook traffic has doubled in that time frame but still represents a fraction of Virgin Media's overall DNS traffic. YouTube grew from 0.5 percent to 0.75 percent of the carrier's DNS traffic, while Facebook grew from 0.5 percent to 1 percent.
In contrast, MySpace now represents 10 percent of Virgin Media's DNS traffic, up from 7.2 percent last fall.
The social-networking sites "are generating much more DNS queries per user than other sites," says Keith Oborn, network systems product architect with Virgin Media. "Because of the way MySpace pages are structured, a single page can generate hundreds of DNS queries."
Oborn says the fact that many of these social-networking sites, including MySpace and YouTube, are served by content-delivery networks adds to the DNS traffic.
"They're making use of an awful lot of short TTLs [time to live values]," Oborn says. "That increases the load on the DNS servers. The same thing would happen for an enterprise customer as you see happening on a service provider network."
Oborn says it's rare for one Web site to account for 10 percent of DNS traffic.
"MySpace is the one that everybody knows about," he says. "It's the thing we need to keep a careful eye on in DNS land."
Virgin Media is addressing this phenomenon by upgrading its DNS infrastructure to the latest version of Nominum's software, which uses a technique called Anycast to provide load balancing for improved redundancy. Virgin Media will complete the upgrade this summer.
With the new configuration, Virgin Media says it "could do 2.5 million DNS queries per second, but all we need is 50,000 or 60,000," Obort says. "We have a lot of overcapacity in DNS, which is both cheap and good to have. ... It cost us a few hundred thousand pounds at most."
Virgin Media is anticipating continued growth in its DNS traffic, driven in part by social-networking sites. "Overall our DNS traffic is growing twice as fast as the number of users," Oborn says.
At the University of Kansas, social-networking sites, including MySpace, Facebook and YouTube, are among the 10 most popular destinations for a user population that averages 20,000 per day, including faculty, staff and students.
These sites "generate a lot of DNS requests since each item on the Web pages is spread over dozens and dozens of servers," says Travis Berkley, supervisor of LAN support services at the university.
The school hasn't needed to upgrade its DNS infrastructure yet to handle the extra traffic that social-networking sites generate. It runs BIND Version 9 software for its DNS servers.
"We have two servers that are the primary for campus, and they seem to keep up just fine," Berkley says, adding that "some departments have set up their own workgroup DNS servers."
One advantage for the the university is that it already limits how much Internet bandwidth students can consume from their dorm rooms. So even though the university doesn't limit access to social-networking sites, it can ensure that usage of these sites is limited to a fixed proportion of its Internet bandwidth.
"We did that independent of these sites or even peer-to-peer," Berkley added.
MySpace seems to be the biggest contributor of the social-networking sites in terms of fostering DNS queries. MySpace declined to comment for this article.
"MySpace is really a pain in the butt," says Cricket Liu, vice president of architecture at InfoBlox, which sells DNS appliances to carriers and corporations. "It generates an enormous number of DNS queries because of the way it refers to content. The domain names they are using all seem to be part of their own content-delivery network."
Liu says any organization running a recursive name server will feel the pinch from MySpace's DNS-heavy design. That includes carriers, universities and corporations.
"The recursive name server is ultimately responsible for getting the answer on behalf of the resolver on the laptop or desktop machine," Liu explains. "So it's the one that has to go out and navigate the Internet's name space, find the authoritative name server for MySpace.com and get the data back. Then it has to keep going back to the MySpace.com name servers to resolve the different domain names on a page. ... It might have to hit those MySpace.com name servers 45 times or more for a particular page."
MySpace's own DNS servers are less affected by this situation than those run by carriers or enterprises.
"The amount of horsepower it takes to handle a recursive query is more than it takes to handle an authoritative query," Liu explains. "MySpace has to run name servers that are authoritative for MySpace.com. ... The same piece of hardware can do an order of magnitude more responses when it's authoritative for MySpace.com than it can do acting as a recursive server. That's because it doesn't have to track the ongoing progress of the name resolution process; it just has to answer it."
The impact of sites like MySpace is also minor on the root servers and top-level domains. For example, VeriSign estimates that social-networking sites account for less than 1 percent of the DNS queries at the .com and .net level. VeriSign handles 32 billion DNS queries a day.
Experts agree that carriers and enterprises are the ones that will need to watch their DNS traffic trends in light of the "MySpace Effect."
"The rise of social-networking sites is just one of a number of factors that are causing the increase in DNS queries," Liu says. "Another would be antispam mechanisms and just the increasing penetration of broadband."
And it's not just DNS queries that social-networking sites like MySpace drive, but also large volumes of traffic.
"Social-media sites are driving a fantastic amount of usage," Akamai's Afergan says. "These sites are motivating their users to be interacting with their sites in a very engaging way, which is driving a large experience time."
Afergan says social-networking sites affect network utilization in two ways: the profile-based sites like MySpace generate a lot of requests per user for small files, while the video-based sites like YouTube demand a lot of bandwidth for large video files to be transmitted across the network.
"Most of our networking partners are seeing these sites drive an incredible amount of traffic, both in the number of requests and the bytes involved in those requests," says Afergan.
The heavy network demand of these Web sites is one reason that seven of the top 10 social-networking sites use Akamai's content-delivery service to offload traffic. It's also a reason that many carriers allow Akamai to put edge servers inside their networks to serve up rich content locally.
"Part of what we do for carriers is minimize the traffic on their networks," Afergan says, adding that Akamai's servers also reduce DNS traffic.
The impact of social-networking sites is primarily on carrier and university networks today, but it is likely to affect more corporations as they add social-networking features to their e-commerce and intranet sites.
IBM, for example, runs its own social network called BluePages, which allows employees to provide information about themselves to other employees.
Meanwhile, Coca-Cola this month is set to launch a mobile phone-based social-networking community for Sprite drinkers called Sprite Yard.
"Imagine when there are thousands of these sites," says Ken Silva, CSO of VeriSign. "Then they will be a more significant share of overall DNS queries."
Silva worries more about the impact on DNS from the migration of telephony and television services to the Internet than he does about social-networking sites.
"If one big telephony provider migrates to the Internet, they could bring millions of users and generate big chunks of bursty growth," he says.
VeriSign is in the midst of a three-year, US$100 million upgrade to its DNS infrastructure, which supports the .com and .net registries and two root servers. The upgrade will increase the company's DNS capacity tenfold.
"Planning for these things like social-networking sites and large infrastructure moving to IP is what this upgrade is all about," Silva adds.
For more information about enterprise networking, go to NetworkWorld. Story copyright 2007 Network World Inc. All rights reserved.
Microsoft Better at Patching XP Than Vista
A Microsoft Corp. security executive released data Thursday showing that, six months after shipping Windows Vista, his company has left more publicly disclosed Vista bugs unpatched than it did with Windows XP.
In total, Microsoft has patched 12 out of 27 disclosed Vista vulnerabilities in the six months after it first shipped last November. During XP's first six months, Microsoft's security team patched 36 out of 39 known bugs.
The data was published by Jeff Jones, a Microsoft security strategy director, who said that overall, Vista was doing better than XP. "Windows Vista continues to show a trend of fewer total and fewer high-severity vulnerabilities at the six month mark compared to its predecessor product, Windows XP," he wrote.
Jones didn't address the larger number of unpatched vulnerabilities, but he did note most of the unpatched Vista bugs were not critical. Microsoft had left only one high-severity Vista vulnerability unpatched during the period. At the end of XP's first six months, there were two high-severity bugs that were unpatched.
Microsoft patched 23 high-severity XP bugs during its first six months, compared with only one high-severity Vista flaw.
Jones argued that Vista had a lower number of vulnerabilities than competitive operating system products such as Red Hat Enterprise Linux and Mac OS X.
He published the data in an effort to show how Microsoft's software development methodology, called the Security Development Lifecycle (SDL) is yielding dividends. But his method of comparing Windows to Linux and Mac OS X is problematic, according to some.
"This is an apples-to-oranges comparison," said HD Moore, one of the hackers behind the popular Metasploit penetration testing toolkit. "If you want a more accurate view, try comparing the number of flaws between Microsoft-developed software and vendor-X-developed software. Most Linux vendors don't actually write the majority of the packages they include," he said via e-mail.
"Alternatively, force Microsoft to include all vulnerabilities in common third-party software," he added. "For example, the thousands of exploitable ActiveX controls that... vendors include with a Windows system."
According to Randy Abrams, director of technical education with antivirus vendor Eset LLC, it will be more interesting to look at vulnerability statistics once Vista becomes more popular than XP, and the target of more hackers.
But Microsoft has stepped up its security practices, he added. "I think their Security Development Lifecycle initiative has improved the quality of the code," he said.
Thursday, June 21, 2007
Is video game addiction a psychiatric disorder?
Is video game addiction a psychiatric disorder?
AMA report seeks to declare it one
June 21, 2007 (CHICAGO) - The telltale signs are ominous: teens holing up in their rooms, ignoring friends, family, even food and a shower, while grades plummet and belligerence soars.
Related Links
A leading council of the nation's largest doctors' group wants to have this behavior officially classified as a psychiatric disorder, to raise awareness and enable sufferers to get insurance coverage for treatment.
In a report prepared for the American Medical Association's annual policy meeting starting Saturday in Chicago, the council asks the group to lobby for the disorder to be included in a widely used mental illness manual created and published by the American Psychiatric Association. AMA delegates could vote on the proposal as early as Monday.
It likely won't happen without heated debate. Video game makers scoff at the notion that their products can cause a psychiatric disorder. Even some mental health experts say labeling the habit a formal addiction is going too far.
Dr. James Scully, the psychiatric association's medical director, said the group will seriously consider the AMA report in the long process of revising the diagnostic manual. The current manual was published in 1994; the next edition is to be completed in 2012.
Up to 90 percent of American youngsters play video games and as many as 15 percent of them -- more than 5 million kids -- may be addicted, according to data cited in the AMA council's report.
Joyce Protopapas of Frisco, Texas, said her 17-year-old son, Michael, was a video addict. Over nearly two years, video and Internet games transformed him from an outgoing, academically gifted teen into a reclusive manipulator who flunked two 10th grade classes and spent several hours day and night playing a popular online video game called World of Warcraft.
"My father was an alcoholic ... and I saw exactly the same thing" in Michael, Protopapas said. "We battled him until October of last year," she said. "We went to therapists, we tried taking the game away.
"He would threaten us physically. He would curse and call us every name imaginable," she said. "It was as if he was possessed."
When she suggested to therapists that Michael had a video game addiction, "nobody was familiar with it," she said. "They all pooh-poohed it."
Last fall, the family found a therapist who "told us he was addicted, period." They sent Michael to a therapeutic boarding school, where he has spent the past six months -- at a cost of $5,000 monthly that insurance won't cover, his mother said.
A support group called On-Line Gamers Anonymous has numerous postings on its Web site from gamers seeking help. Liz Woolley, of Harrisburg, Pa., created the site after her 21-year-old son fatally shot himself in 2001 while playing an online game she says destroyed his life.
In a February posting, a 13-year-old identified only as Ian told of playing video games for nearly 12 hours straight, said he felt suicidal and wondered if he was addicted.
"I think i need help," the boy said.
Postings also come from adults, mostly men, who say video game addiction cost them jobs, family lives and self-esteem.
According to the report prepared by the AMA's Council on Science and Public Health, based on a review of scientific literature, "dependence-like behaviors are more likely in children who start playing video games at younger ages."
Overuse most often occurs with online role-playing games involving multiple players, the report says. Blizzard Entertainment's teen-rated, monster-killing World of Warcraft is among the most popular. A company spokesman declined to comment on whether the games can cause addiction.
A woman in the New Haven, Conn., area who bought the game for her 15-year-old son last year, says he got hooked on it.
"Now that I look back on it, it's like I went out and bought him his first Jack Daniel's," said the 49-year-old woman who didn't want her name used to spare her son from ridicule.
Dr. Martin Wasserman, a pediatrician who heads the Maryland State Medical Society, said the AMA proposal will help raise awareness and called it "the right thing to do."
But Michael Gallagher, president of the Entertainment Software Association, said the trade group sides with psychiatrists "who agree that this so-called 'video-game addiction' is not a mental disorder."
"The American Medical Association is making premature conclusions without the benefit of complete and thorough data," Gallagher said.
Dr. Karen Pierce, a psychiatrist at Chicago's Children's Memorial Hospital, said she sees at least two children a week who play video games excessively.
"I saw somebody this week who hasn't been to bed, hasn't showered...because of video games," she said. "He is really a mess."
She said she treats it like any addiction and creating a separate diagnosis is unnecessary.
Dr. Michael Brody, head of a TV and media committee at the American Academy of Child and Adolescent Psychiatry, agreed. He praised the AMA council for bringing attention to the problem, but said excessive video-game playing could be a symptom for other things, such as depression or social anxieties that already have their own diagnoses.
"You could make lots of behavioral things into addictions. Why stop at video gaming?" Brody asked. Why not Blackberries, cell phones, or other irritating habits, he said.
On the Net:On-Line Gamers Anonymous: http://www.olganon.org
(Copyright 2007 by The Associated Press. All Rights Reserved.)
Wednesday, June 20, 2007
DOJ Pushes Microsoft to Produce Vista SP1 in '07
It's unusual, but confirmation of the availability of Windows Vista's first service pack came not from Microsoft Corp., but from the U.S. Department of Justice.
Gregg Keizer, Computerworld
Wednesday, June 20, 2007 11:00 AM PDT
It's unusual, but confirmation of the availability of Windows Vista's first service pack came Tuesday not from Microsoft Corp., but from the U.S. Department of Justice.
Tucked into the government's 27-page joint status settlement report released late Tuesday was evidence that Microsoft will put the beta of Vista SP1 into users' hands before the end of the year. The report also confirmed Windows XP SP3, but did not specify beta or final release dates, although it said some code would be finalized this summer.
Microsoft has been loath to talk about either service pack, but has been particularly mum about Windows Vista SP1, a widely-anticipated bug update that some enterprise users are waiting on before deploying the new operating system.
As recently as April, when Intel Corp.'s CEO Paul Otellini hinted that Vista SP1 would likely release in October or November, Microsoft refused to confirm any schedule. "We will continue to take customer feedback from programs like the TAP [Technology Adoption Program], and will ultimately determine an official delivery date as the service pack is nearer to completion," a company spokeswoman said at the time.
In the compromise struck between Microsoft and state and federal antitrust regulators, the company must make changes to Vista's desktop search tool so users and OEMs can pick a default search and indexing program to replace Vista's baked-in software for running Start menu searches. The user- or OEM-selected default must also be an option in searches initiated from Windows Explorer or the Control Panel.
"Microsoft will deliver the required changes in Service Pack 1 of Windows Vista, which Microsoft currently anticipates will be available in beta form by the end of the year," the report stated twice, albeit in slightly-different phrasing each time.
The changes to Vista's desktop search were prompted by a complaint filed by Google, Inc. in late 2006. That complaint accused Microsoft of designing Vista to discourage users from running other developers' indexing and search software. Specifically, Google charged that turning off Vista's desktop search was too difficult for many users, and that with two indexers running -- Microsoft's and Google's, presumably -- PC performance suffered, a side-effect Google said convinced some users not to run its Desktop search application.
Microsoft will be held to its promise to deliver the search changes, the report hinted. "Plaintiffs are collectively satisfied that this agreement will resolve any issues the complaint may raise, provided that Microsoft implements it as promised," regulators said.
Windows XP SP3 also gets a mention in the status report. In earlier updates filed with Judge Colleen Kollar-Kotelly, who oversees the 2002 consent decree, Microsoft was ordered to make changes to Windows XP, an OEM pre-installation kit, and other software, including Internet Explorer. "Nearly all outstanding issues have been resolved and the remaining issues will be addressed in the coming weeks," the report said.
According to the May 2006 status update, the government's technical committee was still discussing with Microsoft changes to XP's "Set Program Access and Defaults" feature, a tool that lets users choose default programs for browsing, e-mailing, instant messaging, and playing CDs.
Although Microsoft confirmed plans to crank out a Windows XP SP3 as long ago as October 2005, it recently reiterated that it wouldn't release the update until sometime in the first half of 2008. The XP modifications mandated by the technical committee, however, are to be finished this summer.
"The Windows XP changes will be incorporated into SP3 for Windows XP," said the report. The changes to the code will be available for review by the TC this summer... [and] the changes... will remain in the final release of SP3."
Google Complaint Triggers Vista Desktop Search Revision
Changes to come in Microsoft Windows Vista will allow users to select a default desktop search program that's not Windows Instant Search.
Grant Gross, IDG News Service
Wednesday, June 20, 2007 10:00 AM PDT
Microsoft Corp. will change how desktop search works in its Vista operating system by the end of the year, in response to an antitrust complaint by rival Google Inc., the company said in court documents released late Tuesday.
Microsoft has agreed to make changes that would allow end users and OEMs (original equipment manufacturers) to select a default desktop search program in Vista that's not Windows Instant Search, according to a status report in the ongoing court review of Microsoft's 2002 antitrust settlement with the U.S. Department of Justice. The change will come in Windows Vista Service Pack 1, due out in beta form by the end of 2007.
"Microsoft believes that Google's complaint is without merit," Microsoft's lawyers wrote in the status report, filed with the U.S. District Court for the District of Columbia. "Nevertheless, Microsoft worked with the Plaintiffs in a spirit of cooperation to resolve any issues the complaint may raise."
Google, in a statement, said the search changes are welcome, but more needs to be done.
"Microsoft's current approach to Vista desktop search clearly violates the consent decree and limits consumer choice," David Drummond, Google's senior vice president and chief legal officer, said in the statement. "These remedies are a step in the right direction, but they should be improved further to give consumers greater access to alternate desktop search providers."
Earlier this month, Google confirmed that it had complained to the DOJ about Vista's desktop search functionality. Google had complained that it was difficult to replace Vista's search with products from Google or other competitors.
In the 2002 settlement, Microsoft agreed to allow competing middleware vendors to easily replace Microsoft software with their own in Windows operating systems.
As part of the desktop search agreement, software vendors will be able to register their products as alternatives for the Vista search. The default search selected by the computer user or OEM will launch whenever Vista launches a search result window, and the default search will have space in Vista's start menu
Microsoft will also tell software vendors and OEMs that the desktop search index in Vista is designed to run in the background and "cede precedence over computing resources to any other software product, including third-party search products," the DOJ said in its portion of the status report. "Microsoft will emphasize that there is no technical reason why OEMs and end users cannot, if they choose to, install additional desktop search products on their systems."
Microsoft will also provide technical information to allow other desktop search providers to design their products to optimize computer resources, the DOJ said.
The plaintiffs in the case, including 17 states that sued Microsoft for antitrust, are "collectively satisfied that this agreement will resolve any issues" in the Google complaint, the DOJ said.
Elsewhere in the status report, the DOJ said a technical committee overseeing Microsoft's compliance has hired two consulting firms to check Microsoft's procedures for identifying communications protocols that it is required to disclose to independent software vendors who want to make their products interoperable with Microsoft's. In March, Microsoft and the plaintiffs reached an agreement to address concerns over the belated discovery of protocols that plaintiffs believed needed to be disclosed.
The technical committee will extend a royalty-free program for software vendors to receive the protocols, the DOJ said. The royalty-free program will continue 18 months after the date the committee decides the protocol documentation is substantially complete, and the technical committee can extend the program if it believe Microsoft isn't making progress on the documentation, the DOJ said.
But Microsoft is on schedule with a plan to fix technical documentation used by other software vendors, the DOJ said. Errors in the technical documentation have prompted repeated complaints from the antitrust plaintiffs in recent months, but the DOJ said Microsoft has been able "to keep up with the flow of new technical documentation issues."
Tuesday, June 19, 2007
Accelerate Windows by Tweaking Virtual Memory
If you have only one hard drive, just leave well enough alone. But if you have two or more internal or external hard drives (not just disk partitions), your PC will be peppier if you keep the default paging file (what Microsoft calls the virtual memory disk space) on your boot drive (the one that holds Windows) and add a paging file to the second drive.
To do so, log in to Windows as an administrator and verify that you have more than one hard drive in your computer: Click Start, Run (just Start in Vista), type diskmgmt.msc, and press
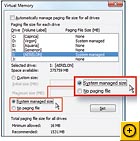
Bonus tip: In Vista, you can open the System Properties dialog box directly to the Advanced tab by clicking Start, typing
systempropertiesadvanced, and pressing In the Performance section, click Settings (Performance Options in Windows 2000) and then the Advanced tab (in XP and Vista). Under Virtual Memory, click Change. In Vista, uncheck Automatically manage paging file size for all drives. You'll see a paging file size already listed on your Windows drive; leave it alone, or Windows won't be able to create a memory dump file with debugging info in the event of a particular type of system error.
Next, in the drive list select a partition on a different drive where you want to add another paging file. Select Custom size if you want to set the size yourself and type in the initial and maximum size (Microsoft says making them the same amount is most efficient); Microsoft's rule of thumb is to make the file 1.5 times the amount of RAM in your system. Or select System managed size to let Windows determine the size (XP and Vista only). Click Set, then OK.
If the partition you selected contains another installation of Windows, you'll receive an error message warning that the file pagefile.sys already exists there. As long as the two operating systems are not running at the same time using virtualization software, it's safe for you to overwrite or delete pagefile.sys, since Windows will re-create the file automatically the next time you boot that partition's Windows installation.
You'll see a reminder that the changes will take effect the next time you restart your system. Windows will most often use the paging file on the least-busy drive, which means your new paging file will do most of the work.-----------------------------------------------------------------------------------------------
Get a Free Mac on Your PC
Admit it: You're secretly humiliated by those TV commercials with the two guys pretending to be a Mac and a PC. Don't let your Mac envy get the better of you; download FlyakiteOSX, which goes beyond skinning to transform your entire XP interface into a near-perfect replica of Mac OS X. FlyakiteOSX converts sounds, cursors, title bars, icons, startup and log-in screens, and more. It even has an OS X-like dock for launching and managing running applications. And it's free!
Monday, June 18, 2007
A gaming PC at a reasonable price
A. Online games such as World of Warcraft, Everquest and City of Heroes are gaining popularity. Some PC makers have taken advantage of this growing market with systems that satisfy gamers' hunger for bleeding edge technology.
But specialty gaming systems can be expensive. You can keep the cost of a game-capable PC reasonable by knowing what to look for. You don't need bleeding edge technology and you don't have to spend a fortune.
Multiplayer online games tend to be relatively forgiving on minimum requirements. Many online games, including those that I've mentioned, will do with an 800 MHz processor such as Pentium 3, 512 megabytes of RAM and graphics cards that passed their prime four or five years ago.
There are a few reasons why you should aim to outdo these bare-minimum requirements. Unlike stand-alone games, online games continually change, improve or expand. That means that the requirements can become more demanding.
As your son probably knows, minimum requirements also mean doing without features like lighting effects and scenery details. They can also mean long loading times between different game levels or scenes. In short, this breaks the immersion that gamers seek.
Finally, consider the life of the computer. The closer you can get to top-of-the-line, the longer your son's computer will last against the demands of future software and technology. To get the most for your money, however, stay a notch under the top-of-the-line.
A strong gaming PC should have a microprocessor from Intel or Advanced Micro Devices. I would look for a microprocessor that is a few steps down from the top. The computer also needs 1 GB of RAM. Graphics cards (also called video cards) are harder to specify. In general, look for one that includes 256 MB of its own memory. The most popular graphics equipment is produced by NVIDIA and ATI.
Such a desktop system should cost between $1,000 and $1,500 from online retailers. For an equivalent laptop, expect prices just under $2,000.
One possible complication is the release of Vista, the newest version of Windows. Vista will eat up more of a computer's resources than XP. If your son plans to upgrade to Vista, consider an even more capable system.
You can read the details on Vista's requirements in my recent column. For games, XP should suffice for at least the next few years.
Another source of confusion may be the continuing trend toward multi-core processors. You can learn about that here.
And for more information, check out a Buying Guide on gaming computers.
Get rid of uninstalled programs
This uninstaller can do the same job as Windows' Add or Remove Programs. It also adds a few extra features. It includes checkboxes beside each program in the list. You can select all of the programs you'd like to uninstall at once. It also includes a backup feature so that you can undo hasty uninstalls.
Finally, Easy Uninstaller offers a one-click way to get rid of listings that try to stick around after the related program has been uninstalled.
Cost: Free
Erase a whole hard drive
This program can make those deleted files unrecoverable by overwriting them with meaningless data. It can wipe out everything, including Windows, to leave an essentially blank disk.
KillDisk can be put on a floppy disk. The disk can be used to boot up the computer and erase everything on the hard drive. Make sure you've made copies of anything to need to save on your new computer!
Cost: Free
Link: www.killdisk.com
FBI to Battle Zombie Horde
FBI to Battle Zombie Horde
Thu Jun 14, 2007 11:03PM EDT
You may not know that your computer is sending spam, being used as a pawn in coordinated internet attacks, hosting illegal files, or otherwise part of the malware-distribution network known as the zombie horde. Some estimates peg the number of email spams sent each day at around 55 billion, the vast majority of which are sent by infected PCs, usually without any knowledge of it by their owner.
It's all part of what's known as a botnet, giant networks of malware-infected PCs that act as slaves to a master controller via the internet. These PCs, called zombies, are perhaps the biggest security threat on the internet today.
And now the FBI wants to do something about it. How? It's directly contacting a million PC owners to let them know what they ought to have known all along: That their computers are infected and are being hijacked for nefarious uses. The goal is to help track down the source of these infections and put the hackers responsible behind bars. "Operation Bot Roast" (love the name) has already led to the arrest of three scammers.
The feds have offered the same general advice that I do to those infected: Protect yourself against malware and viruses by using the appropriate security tools, and take extra precautions if you find your PC running slowly or sending emails you didn't create (check your Sent Items folder!).
Sunday, June 17, 2007
Monitor startup programs
Windows allows you to inspect programs currently running. But it doesn't offer a way to stop new programs from adding themselves to the automatic startup list.
That's where StartupMonitor comes in. It alerts you to any additions to Windows' automatic startup programs. The alerts give you the power to allow or deny the program from starting automatically with Windows.
StartupMonitor is small and runs in the background. It starts automatically with Windows, which is a little ironic.
Cost: Free
Link: www.mlin.net
Prevent new startup programs
You could check for signs of additional startups each time you install a new program. But if you install new programs as frequently as I do, the constant checking becomes a hassle.
Startup Monitor takes the work out of monitoring for unwelcome startup programs. Any time a program tries to add itself as an automatic startup, Startup Monitor will alert you with a small pop-up.
On each alert, you'll see the name of the program along with options to allow or deny the program from starting automatically with Windows.
Cost: free, donations accepted
Link: www.windowsstartup.com
Recover lost files
Fortunately, it's often possible to undo accidental deletions. Deleted data stays on the hard drive until Windows uses the space for new files. But Windows won't let you browse these areas of the hard drive. To do that, you'll need a file recovery program.
Recuva is a free, no-frills file recovery program. Just choose a drive, if you have multiple hard drives. Then click the Scan button. Recuva lists any deleted data that can be recognized as files. It also rates the condition of each file. Some files may already be partially overwritten.
A checkbox accompanies each item in the list. Just select which you want to recover and click the Recover button. Recuva prompts you for a place to save the recovered files.
Recuva is still in its beta (testing) phase, so it's not perfect. For example, I noticed a few scrambled file names in the results list. Nevertheless, they and the other files I recovered were complete and undamaged.
Recuva works on Windows XP or 2000.
Cost: Free
Link: www.recuva.com
Saturday, June 16, 2007
A quick way to send large files
And don't even think of sending your photos and videos the old-fashioned way -- your friends and family want to see them now!
So try YouSendIt. You can send files of up to 1 GB. The files remain accessible for seven days or for 25 downloads, whichever comes first. They are then deleted.
Keep in mind, though, you may not want to send any confidential files through this services. You just never know...
Cost: Free
Create your own Web pages
You don't even have to know HTML (HyperText Markup Language). You just need to know how you want your page to look.
Nvu has features comparable to FrontPage and even Dreamweaver. But Nvu is free, which is great for those of us without a professional-sized budget.
Using Nvu is no more difficult than using a word processor. You can add text, pictures, links and buttons to your Web pages. Nvu also lets you customize details like colors and fonts. It even includes a spellchecker that underlines possible mistakes as you type. Nvu is a WYSIWYG (what-you-see-is-what-you-get) program. So the way you build a Web page is the way it will look online!
Nvu is also great for those of you who already have some Web design skills. It lets you instantly switch between the Web page preview and the actual HTML. You can edit the HTML as you like or insert scripts. Then you can see your changes immediately. Nvu also supports CSS (cascading style sheets). When you finish, you can upload your pages using the built-in FTP site manager. Works with Windows 98/2000/Me/XP OS X 10.1.5 or later.
Cost: Free
Link: www.nvu.com
Don't be tracked on the Internet
These files are created by Internet Explorer. They contain private information about the sites you visit. They can even contain personal information about your computer and e-mail usage. You cannot remove Index.dat files by deleting your cookies, files or clearing your history.
However, Index.dat Suite will delete these Index.dat files, and keep your information secure. It can also delete temporary internet files, temp files, cookies and history files. Use the program to view the Index.dat files on your system. And don't worry; deleting these files will not harm your computer.
Cost: Free
Link: support.it-mate.co.uk
Cutting down on CO2 emissions
All kidding aside, this looks like a serious problem. And among the contributors are our many gadgets. How many things do you charge overnight? How many of your digital devices are sipping electricity, waiting for you to pick up the remote?
I'm not sure how we can undo modern times. But maybe we can cut down on power used by our computers.
I leave my boxes on most of the time. Admittedly, that wastes electricity. Windows has built-in devices to save power. But they aren't terribly reliable, in my experience.
So I was happy to find the CO2 Saver. This little program throttles down your power usage when you're not around. As a bonus, it shows how much CO2 you've saved.
CO2 Saver is easy to install. It sits in the notification area—the bottom right of your desktop. Best of all, it's free!
Cost: Free
Link: co2saver.snap.com
Test your PC's RAM
So it is important to test your computer's memory. After downloading this file, save the file to a CD for booting.
You can also download a small program that will do this step for you. Then you can find out if a bad RAM module is the root of your problem.
Memtest86 offers a great way to test your computer's memory.
www.memtest.org
Wednesday, June 13, 2007
After eBay Pulls Ads, Google Cancels Offending Party
Lesson learned: Google has realized its party to attract eBay sellers may have been in bad taste
Juan Carlos Perez, IDG News Service
Wednesday, June 13, 2007 4:00 PM PDT
A contrite and repentant Google canceled a party that irked eBay and that a source said led eBay to remove all of its ads from Google's U.S. network earlier this week.
On Monday, Google announced it would throw a party in Boston on Thursday evening designed to attract eBay merchants who would be in town to attend the eBay Live annual seller conference.
The purpose of the party: protesting eBay's decision to forbid merchants in its marketplace from using Google's Checkout online transaction system.
EBay found Google's move to be in bad taste and, at some point after the party was announced, eBay took the drastic measure of pulling all of its ads from Google's AdWords U.S. network.
Read the original story here.
A source familiar with the situation said that the decision to turn off the ads had come from eBay's top executives who were steaming over what they perceived as a low blow by Google designed to embarrass eBay in front of its top merchants.
It would be hard to disagree with eBay executives' assessment, considering the mocking tone of Google's party announcement , encouraging eBay merchants to gather at the Old South Meeting House, where in 1773 mass protest meetings were held, leading to the Boston Tea Party.
"We'll use the same spot where revolutionaries launched the Boston Tea Party to celebrate freedom with free food, free drinks, free live music -- even free massages," the official blog posting reads.
Then, on Wednesday afternoon, Google unexpectedly cancelled the party, after its officials apparently determined they had gone too far.
"eBay Live attendees have plenty of activities to keep them busy this week in Boston, and we did not want to detract from that activity. After speaking with officials at eBay, we at Google agreed that it was better for us not to feature this event during the eBay Live conference," reads a posting on that same blog.
EBay, which had earlier blasted Google for the planned party, said it was pleased with Google's decision. "It's reassuring to see that Google recognizes that their actions were inappropriate. We're pleased that our partner chose to do the right thing and cancel their event," eBay said in a statement.
However, eBay is keeping its ads off AdWords, eBay spokesman Hani Durzy said. EBay Live begins Thursday in Boston.
The spat is yet another sign of what many consider a significant deterioration of relations between the two Internet giants in recent years, as Google has become a partial competitor to eBay.
Earlier Wednesday, Durzy said the decision to pull out the ads wasn't related to the party and characterized it as an ordinary experiment by eBay, similar to others the company constantly does to determine the best allocation of its advertising and marketing budget.
But there is nothing ordinary about eBay and Google, and the pullout is likely to have significant repercussions for both companies while it lasts: EBay is the largest paid search advertiser in the U.S. and Google is the country's largest paid search ad network.
In March, eBay ranked first in the U.S. among paid search advertisers with 802 million sponsored link exposures, or 4.1 percent of the total, according to comScore Networks Inc. That doesn't even take into account eBay's comparison shopping engine, Shopping.com, which ranked third on that list with 357 million sponsored link exposures, or 1.8 percent of the total.
Meanwhile, Google topped the list of search engine referrers, handling 57.3 percent of all paid search ad clickthroughs, comScore said. Yahoo Inc. took a distant second place with 26.1 percent of clickthroughs.
At the center of this week's confrontation is Google's Checkout online transaction system, introduced about a year ago and so far banned from the eBay sites. EBay argues Checkout doesn't have enough of a track record yet, while Google charges eBay with trying to protect its own PayPal online payment system. In addition to Checkout, Google has been entering eBay territory with other products like its Base listings service.
In May of last year, eBay and Yahoo struck a wide-ranging partnership that, among other things, made Yahoo the exclusive provider of search and display ads within U.S. eBay sites.
Although Google performs a similar function for eBay sites outside of the U.S., the eBay-Yahoo tie up was seen as a defensive move by eBay and Yahoo against Google.
Google hasn't replied to requests seeking comment.
Microsoft unveils patch package
Windows users are being urged to install the June package of security patches from Microsoft.
The security update contains six patches which close 15 vulnerabilities found in a variety of Windows programs.
The patches help to shut loopholes in Internet Explorer, Outlook Express, Windows Mail and Windows Vista.
More than half the loopholes are rated as "critical" which often means they can be exploited without a PC owner's knowledge or consent.
Secure channel
Malicious code to exploit one of the vulnerabilities in the package is already known to be circulating online.
Using this code hi-tech criminals could craft e-mail messages or booby-trapped webpages that could take over PCs.
Some of the vulnerabilities fixed by the patch rated as "critical" are for various versions of Internet Explorer including the one that runs on the Vista operating system.
Vista, the latest edition of Microsoft's operating system, gets a patch for itself which aims to stop malicious hackers exploiting a loophole to steal administrative passwords.
Included in the bundle is a patch that tackles a serious problem in the way that Windows handles part of a program called the Windows Secure Channel.
This vulnerability could be targeted by malicious hackers as it is used by many websites to handle security certificates and keep user data confidential.
Windows users can get hold of the patches by turning on the automatic update feature in the operating system or by visiting the Microsoft Update site and downloading them.
The second Tuesday of every month is the date on which Microsoft typically issues security patches for its software programs.